功能介绍
在某些情况下,通过需要通过IPSEC VPN加密的数据,其源或目的地址为多个不同的网段,此时就在配置IPSEC感兴趣流时就需要将所有的网段都定义进来,这就是IPSEC多感兴趣流。
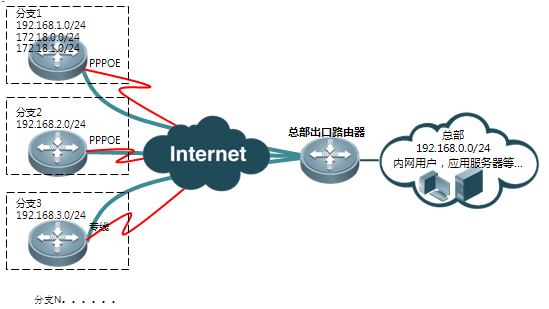
一、组网需求:
分支1存在192.168.1.0/24、172.18.0.0/24、172.18.1.0/24这3个网段,这3个网段都需要访问总部的192.168.0.0/24,并且互访的数据需要通过IPSEC VPN进行加密。
二、组网拓扑:
三、配置要点:
1、配置基本的IPSEC功能
2、在分支1上配置IPSEC多感兴趣流
注意:
RSR10/20 10.3(5b6)之前的版本、RSR30 10.4(3b11)之前的版本、RSR50/RSR50E的多感兴趣流配置方法与本文提供的配置方法不同,具体请参考附录。
四、配置步骤
1、配置基本的IPSEC功能
根据现场环境及客户需求,选择合适的IPSEC部署方案,详细配置参考IPSEC“基础配置”章节(典型配置--->安全--->IPSEC--->基础配置)
2、在分支1上配置IPSEC多感兴趣流
多感兴趣流的配置与单感兴趣流的配置唯一不同之处,就是在配置感兴趣流的ACL时,将所有网段的流量定义进去:
ip access-list extended 101
10 permit ip 192.168.1.0 0.0.0.255 192.168.0.0 0.0.0.255
10 permit ip 172.18.0.0 0.0.0.255 192.168.0.0 0.0.0.255
10 permit ip 172.18.1.0 0.0.0.255 192.168.0.0 0.0.0.255
五、配置验证
完成配置后,在分支1上发起感兴趣流触发IPSEC协商成功后,可以看到分支1与总部间协商成功了多个ipsec sa,每个ipsec sa对应着1对感兴趣流:
site1#ping 192.168.0.1 so 192.168.1.1
Sending 5, 100-byte ICMP Echoes to 192.168.0.1, timeout is 2 seconds:
< press Ctrl+C to break >
.!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/8/10 ms
site1#ping 192.168.0.1 so 172.18.0.1
Sending 5, 100-byte ICMP Echoes to 192.168.0.1, timeout is 2 seconds:
< press Ctrl+C to break >
.!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/8/10 ms
site1#ping 192.168.0.1 so 172.18.1.1
Sending 5, 100-byte ICMP Echoes to 192.168.0.1, timeout is 2 seconds:
< press Ctrl+C to break >
.!!!!
Success rate is 80 percent (4/5), round-trip min/avg/max = 10/15/20 ms
site1#show crypto isakmp sa
destination source state conn-id lifetime(second)
10.0.0.1 10.0.0.2 IKE_IDLE 0 86192 //生成1个isakmp sa
site1#show crypto ipsec sa
Interface: FastEthernet 0/0
Crypto map tag:mymap
local ipv4 addr 10.0.0.2
media mtu 1500
==================================
sub_map type:static, seqno:10, id=3
local ident (addr/mask/prot/port): (192.168.1.0/0.0.0.255/0/0))
remote ident (addr/mask/prot/port): (192.168.0.0/0.0.0.255/0/0)) //针对第1条感兴趣流生成的ipsec sa
PERMIT
#pkts encaps: 9, #pkts encrypt: 9, #pkts digest 0
#pkts decaps: 9, #pkts decrypt: 9, #pkts verify 0
#send errors 1, #recv errors 0
Inbound esp sas:
spi:0x4b8e642c (1267622956)
transform: esp-3des
in use settings={Tunnel Encaps,}
crypto map mymap 10
sa timing: remaining key lifetime (k/sec): (4606997/3388)
IV size: 8 bytes
Replay detection support:N
Outbound esp sas:
spi:0x36ee6e8e (921595534)
transform: esp-3des
in use settings={Tunnel Encaps,}
crypto map mymap 10
sa timing: remaining key lifetime (k/sec): (4606997/3388)
IV size: 8 bytes
Replay detection support:N
==================================
sub_map type:static, seqno:10, id=4
local ident (addr/mask/prot/port): (172.18.0.0/0.0.0.255/0/0))
remote ident (addr/mask/prot/port): (192.168.0.0/0.0.0.255/0/0)) //针对第2条感兴趣流生成的ipsec sa
PERMIT
#pkts encaps: 14, #pkts encrypt: 14, #pkts digest 0
#pkts decaps: 14, #pkts decrypt: 14, #pkts verify 0
#send errors 1, #recv errors 0
Inbound esp sas:
spi:0x1cdd2b74 (484256628)
transform: esp-3des
in use settings={Tunnel Encaps,}
crypto map mymap 10
sa timing: remaining key lifetime (k/sec): (4606996/3437)
IV size: 8 bytes
Replay detection support:N
Outbound esp sas:
spi:0x62a1a190 (1654759824)
transform: esp-3des
in use settings={Tunnel Encaps,}
crypto map mymap 10
sa timing: remaining key lifetime (k/sec): (4606996/3437)
IV size: 8 bytes
Replay detection support:N
==================================
sub_map type:static, seqno:10, id=5
local ident (addr/mask/prot/port): (172.18.1.0/0.0.0.255/0/0))
remote ident (addr/mask/prot/port): (192.168.0.0/0.0.0.255/0/0)) //针对第3条感兴趣流生成的ipsec sa
PERMIT
#pkts encaps: 4, #pkts encrypt: 4, #pkts digest 0
#pkts decaps: 4, #pkts decrypt: 4, #pkts verify 0
#send errors 1, #recv errors 0
Inbound esp sas:
spi:0x1b614775 (459360117)
transform: esp-3des
in use settings={Tunnel Encaps,}
crypto map mymap 10
sa timing: remaining key lifetime (k/sec): (4606998/3556)
IV size: 8 bytes
Replay detection support:N
Outbound esp sas:
spi:0x390bcf20 (957075232)
transform: esp-3des
in use settings={Tunnel Encaps,}
crypto map mymap 10
sa timing: remaining key lifetime (k/sec): (4606998/3556)
IV size: 8 bytes
Replay detection support:N
六、附录
1、老版本多感兴趣流的配置方法
注:老版本包括RSR10/20 10.3(5b6)之前的版本、RSR30 10.4(3b11)之前的版本、RSR50/RSR50E